![]()
NDB Quarterly Statistics Report for July – September released
The Office of the Australian Information Commissioner (OAIC) released their third quarterly statistics report for notifications received under the Notifiable Data Breaches (NDB) scheme in late November of 2018. This particular quarter saw:

The vast majority of the breaches saw between 1-1000 individuals impacted by the breach, with the range of 1-10 individuals accounting for 41% of the reported breaches. 85% of the breaches involved the loss of contact information, while 45% included financial details and 35% included identity information. While 57% of the breaches were caused by malicious or criminal attacks, the 37% that were caused by human error shows that we have some way to go with our education and enablement programs, as well as the deployment of technical controls to act as a backstop in such cases.
The following chart breaks down the malicious or criminal attacks, clearly demonstrating that the majority of such cyber incidents were caused by phishing or password brute-force attacks, for which the deployment of multi-factor authentication (MFA) is a very effective mitigating control, along with a solid and ongoing employee awareness campaign.
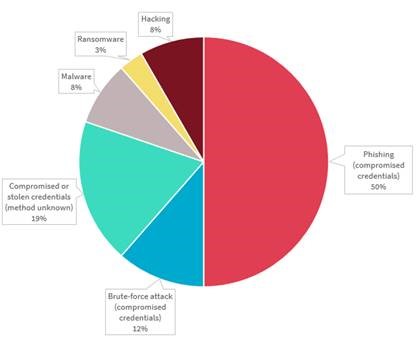
On the plus side, this quarter saw only a marginal increase in the number of reported incidents, from 242 last quarter to 245 this quarter. On the down side, the number didn’t go backwards. For those who are interested in reading the full report, you can find it here.
Texas Instruments Leave Aruba, Cisco and Cisco Meraki WiFi AP's Vulnerable
Dark Reading have reported that researches at Armis, an IoT security company, have found 2 separate vulnerabilities in Texas Instruments Bluetooth Low Energy (BLE) chips that are used in WiFi access points (AP's) manufactured by Aruba, Cisco and Cisco Meraki. These three vendors account for roughly 70% of the enterprise WiFi AP market.

The vulnerabilities are called “BleedingBit”, and could be exploited by sending a specially-crafted packet or series of packets to the vulnerable AP's. In the first vulnerability, the specially-crafted packets could cause a stack overflow, allowing arbitrary code execution on the AP. The second vulnerability, which only impacts Aruba devices, leverages an Over-the-Air Download (OAD) feature to obtain a hardcoded password and completely overwrite the device’s operating system.
Both Cisco and Aruba have released security advisories on the vulnerabilities. Customers running Cisco or Aruba AP's should review the relevant security advisories for impacted products and follow the vendors’ recommendations to address these vulnerabilities.
An Apple (update) a day keeps the "h4x0r5" away!
Apple have released an update which addresses a number of security vulnerabilities – including information disclosure, code execution and privilege escalation – in their core products, according to Bleeping Computer.
One such issue, CVE-2018-4367, allows remote attackers to initiate a FaceTime call from your device through a code execution vulnerability. There are three other FaceTime memory corruption issues addressed in the updates that could also lead to arbitrary code execution.
Another such issue, CVE-2018-4407, is a heap buffer overflow in a fundamental part of the iOS and macOS operating system’s networking code that allows an attacker on the same WiFi network as the targeted device to crash the device by sending a specially-crafted packet to the target. The researcher who discovered the vulnerability, Kevin Backhouse, says that it “also doesn't matter what software you are running on the device - the malicious packet will still trigger the vulnerability even if you don't have any ports open.” Backhouse also said that “anti-virus software will not protect you: I tested the vulnerability on a Mac running McAfee® Endpoint Security for Mac and it made no difference.”
Apple users are recommended to upgrade their devices to the latest versions to address these security issues.
Australian Defence Ship Builder Austal’s Cyber-Hull Breached
ABC News has reported that Australian defence ship builder Austal has been breached and become the victim of a cyber extortion campaign. The report says that Austal’s Australian data management system had been targeted by an “unknown offender” who made off with “some staff email addresses and phone numbers” and potentially “got access to – or stole – drawings and designs of its ships.” Austal has said that "ship design drawings which may be distributed to customers and fabrication sub-contractors or suppliers are neither sensitive nor classified.” It also said that the offender tried to sell some of the stolen material online “and engage in extortion.”
Austal designs, constructs and maintains the Cape Class Patrol Boat program for Border Force and the Royal Australian Navy, as well as the Guardian Class Patrol Boat for the Commonwealth of Australia. No details have yet been provided on the cause of the data breach.
Contact Us today to find out how Thomas Duryea Logicalis can support you with your organisation's security concerns and posture.



