![]()
You can check out anytime you like; but your details will never leave…
The Marriott Hotel chain announced late last year they had identified a breach in their network that had potentially exposed the contact, passport and travel information details of up to 500 million individuals. What is interesting to note is their acknowledgement of the breach dates back 4 years, based on the forensics undertaken to date. The statistics from the Verizon Annual Breach report state the average time from compromise to detection is in the order of hundreds of days and the below graphic validates those findings.
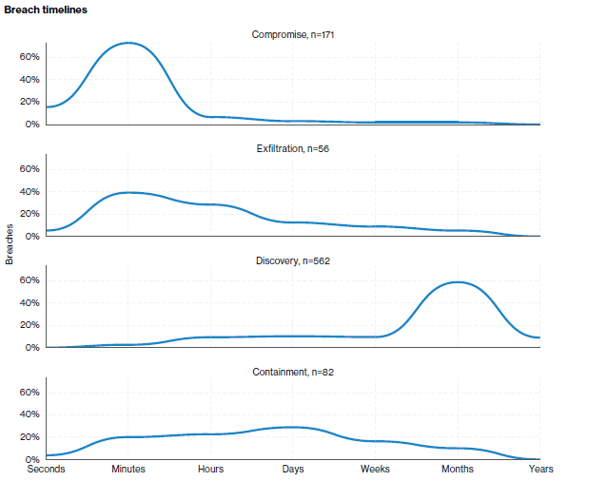
- Source – Verizon Data Breach Investigation Report-2018: https://enterprise.verizon.com/resources/reports/dbir/
The share price dropped from $122 to $113 on the news of the breach which demonstrates the immediate financial impact on the business with inevitable litigation impacting the business further.
Beyond the FAQ provided by the Marriott Hotel, websites such as “Have I Been Pwnd” is a good place to check on a regular basis to determine if your email accounts and potentially other information have been exposed in any breaches.
Containerisation security flaw discovered
A security flaw was announced in the Kubernetes container development platform this week. The vulnerability (CVE-2018-1002105) allows for privilege escalation and can be accessed by both authorised and unauthorised users. For authorised users with "attach," "exec," or "port-forward" privileges, escalating those to admin privileges that allow any process to be executed is trivial.
For anyone at all, an API used in three specific modules will allow a query that returns values that can be used to raise privileges to admin level for any API deployed on the container cluster.
Patches have now been released for these vulnerabilities. This reinforces the need to ensure timely patching and that any patching policy and process extends to Cloud-hosted services and development platforms.
On the first day of Christmas, my Government gave to me, decrypted App security…..
On the last sitting day of the parliamentary year for 2018, weeks before Christmas, a new law known as the “Access and Assistance” bill which allows designated law enforcement agencies to direct a wide range of technology providers (almost all whom use encryption) to help them obtain backdoor access to their products, has been passed by the lower house with ‘amendments’ to be discussed in the new year.
Industry groups, tech experts and civil society organisations have expressed strong concerns about the legislation and the Government's rush to pass it through Parliament. The critics have warned the bill may undermine national security, harm Australian companies and weaken the online security of innocent Australians. How service providers and application vendors delivering apps respond to this legislation will certainly be an interesting topic to follow in the new year. Any application developed in Australia will need to provide the Australian Government with a back-door to communications using that application. How the rest of the world will respond to that requirement is likely to have significant repercussions on the Australian IT industry.
Contact Us today to find out how Thomas Duryea Logicalis can support you with your organisation's security concerns and posture.



