NDB Stats | Q2 2018 Released
Earlier this year OAIC released their NDB Quarterly Statistics Report for the period of 1st April – 30th June, 2018. This is the first full quarter of reporting since the NDB scheme came into effect on 22nd February, 2018.
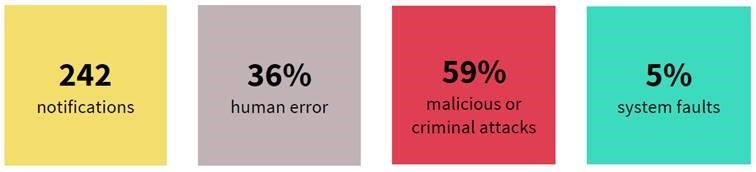
Over the course of the quarter, the number of reported breaches continued to increase, following the trend from the first quarter. March saw 55 breaches reported, with 65, 87, and 90 breaches reported in April, May, and June respectively. The majority of the breaches impacted in the range of 1-100 users, with 52 impacting 101-1000 users and 23 impacting 1001-5000 users. The majority of the breaches involved contact information (216), with the second highest category involving financial details (102).
Of the human-error-initiated breaches, the three most common categories were PI sent to wrong recipient (email), PI sent to wrong recipient (mail), and unauthorised disclosure. Particularly the PI sent to wrong recipient (mail) category, which accounted for 10 cases, goes to prove that we need a mix of administrative controls – including security awareness training – and technical controls to effectively secure our organisations and prevent inadvertent data loss through non-cyber mechanisms.
When it comes to cyber incidents, 77% of reported breaches were due to compromised or stolen credentials through a combination of phishing, brute-force, and unknown attack vectors. The most effective outlet was to reduce the risk associated with credential theft and implementation of MFA, especially on internet-facing services. The takeaway? There are plenty, as the report cuts the statistics in many different ways. Take a look at the report, which can be found here.
Reddit Data Breach
In August, Reddit, among others, reported that Reddit had suffered a data breach that saw a 2007 database backup containing old salted and hashed passwords stolen, as well as some current email addresses.

While Reddit had implemented 2FA (two-factor authentication) for some internet-facing services, they had implemented SMS-based 2FA, which is prone to a number of interception attacks. For this reason, the Australian Signals Directorate does not allow SMS-based 2FA for Level 3 in the Maturity Model.
Reddit have been quick to point out that the attackers did not have write access to their systems, so were not able to modify any of Reddit’s data or configurations. However, they were able make off with a complete backup of a database containing user data from their period of 2005-2007, as well as email addresses used to send out email digests in June 2018. Reddit have emailed any users who may have been impacted by the database component of the breach.
Given that the breach may have involved the PII of EU citizens, there is lots of speculation as to whether they will have a case to answer under the new GDPR rules. Only time will tell. The takeway? Not all 2FA solutions are created equal. As such, ASD restricts Level 3 2FA implementations to the following token types: U2F security keys, physical OTP (one-time password) tokens, biometrics, and/or smartcards.
SamSam
The Hacker News has reported on research carried out by Sophos researchers into the SamSam ransomware, which is currently in its third iteration. As discussed in a previous Security Scan, SamSam has been around since late 2015, starting out as a crypt worm, targeted at the healthcare vertical by exploiting vulnerabilities in JBoss. Since then, SamSam’s TTPs (tools, techniques, procedures) changed to leverage poorly secured RDP/VNC services for initial infection, with human interaction required for privilege escalation and lateral propagation.
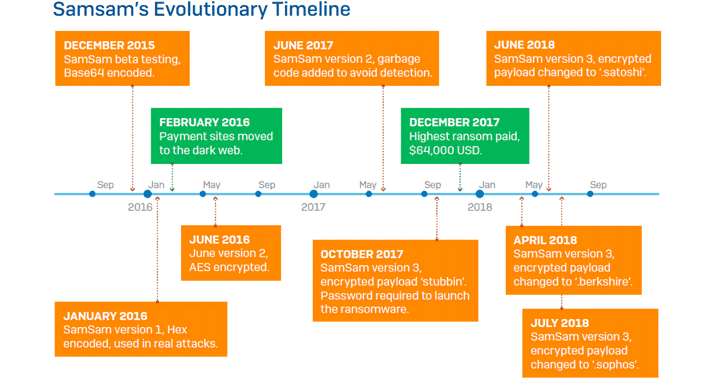
Sophos’ research has show that shadowy figures behind SamSam have netted in the order of $6m from just 233 victims since December 2015. Currently they are netting in the order of $300,000 per month. The takeaway? As recommended earlier, organisations should disable RDP on internet-facing servers, where not required. If RDP cannot be disabled, ensure the use of strong and unique credentials to reduce the risk of credential reuse and brute force attacks.
Contact Us today to find out how Thomas Duryea Logicalis can support you with your organisation's security concerns and posture.



