![]()
Can you run a task for me ASAP?
Over the last couple of weeks, we have seen a number of users across multiple organisations targeted through an email-based social engineering campaign, in which the threat actor starts out with a request that the target “run a task for me ASAP”.

The scam works by using a compromised email account to spoof an email from someone in a position of authority in the target’s organisation, creating a sense of urgency by requesting that the cards be purchased in the next 45 minutes. By claiming that they are in a meeting, the threat actor attempts to avoid the target contacting the spoofed source of the request for validation.

The threat actor then goes on to request that the target purchase a number of Apple iTunes gift cards and send back the validation codes via email.

So, why does the scam work? It’s simple, really – the threat actor takes advantage of a number of cognitive biases. They take advantage of our desire to help others, especially those who are in a position of authority. They take advantage of stress situations and how we react to time pressures. They also take advantage of the fact that the target has most likely been asked to carry out a similar task in the past. In short, they exploit our human vulnerabilities.
So, what can we do to protect ourselves?
- Do not respond to the emails or engage with the threat actor
- If you receive any suspicious emails:
- Sanity check the email:
- Check that the source email matches something that you would expect (e.g. mycompany.com)
- Check for spelling/grammatical errors (e.g. “Can you run a task for me”, “We have some few clients we want to send gift”, etc.)
- Pay attention to your gut – does the request feel right?
- Validate the request with the sender via phone or SMS, using their number that is stored in your corporate address book. Do not use any number that may appear in the email itself, as this could be the threat actor’s number
- Sanity check the email:
- If in doubt follow your organisation’s process for reporting potential phishing emails/security incidents
- If you have been targeted and have responded, please don’t feel silly. This is an example of social engineering at work. These threat actors (attackers) prey on the human vulnerability by knowing what buttons to press. Everybody is susceptible – it is only a matter of finding the right buttons
- Please DO NOT hesitate to contact your IT/Security department – the sooner a threat is known about, the sooner we can investigate and inform others, and the sooner we can take steps to address any deficiencies in our security controls
Vulnerability in Microsoft ADFS Allows Attacker to Bypass MFA
For those of you who have been reading our blogs, you would be aware we are big supporters of MFA. It is one of the most effective controls we can put in place to help mitigate the risk of credential theft and reuse. With that said, what if an attacker managed to steal the credentials of two of your organisation's MFA-enabled users, while also managing to steal the second authentication factor (generally “something owned”, e.g. a hardware token, an SMS or soft token on a phone) for one of the organisation's users? That should mean that the attacker can’t compromise the other user’s account because they don’t have their second authentication factor, correct?
Well, in an article on DARKReading, it has been revealed that a Microsoft ADFS vulnerability would allow exactly this scenario to play out, if the two users are on the same ADFS service. Microsoft have released a patch for this vulnerability which, according to Andrew Lee at Okta, equates to “turning a room key into a master key for every door in the building. Details of the CVE can be found here.
In other 2FA news, Ars Technica has reported that US-based 2FA provider Duo Security is to be acquired by Cisco.
Phishers Bypassing Microsoft Office 365 ATP
The Hacker News is reporting that phishers have found a way to bypass Microsoft Office 365’s Advanced Threat Protection (ATP) mechanism.
Earlier this year, attackers found ways to bypass some of the Office 365 protections using neat little tricks like ZeroFont (inserting hidden words with a font size of zero) and baseStriker (URL splitting). Microsoft has since addressed those issues.
The current attack method involves inserting malicious links into SharePoint documents. A user receiving a collaboration request clicks on the hyperlink in the email, causing their browser to open the SharePoint file. The user is then presented with what looks like a OneDrive “Access Document” request, but the hyperlink leads to user to a phishing site that asks the user to log in with their Office 365 credentials. The pages presented to the user can be seen in the screenshots from The Hacker News’ article reproduced below.
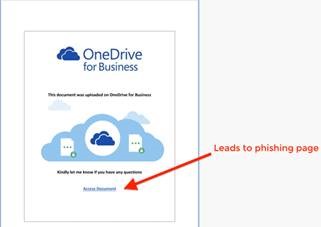
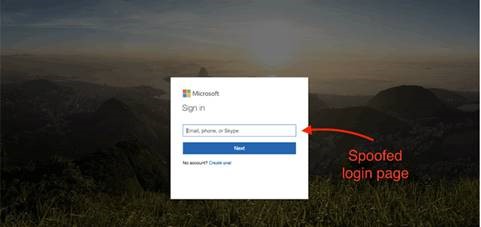 `
`
As Safe Links, Safe Attachments and ATP don’t scan links embedded in shared SharePoint documents, users are not protected from this kind of attack if using these protections alone. This attack method goes to demonstrate the need for multi-layered security in our organisations, so that malicious content can be detected and blocked at time of delivery and time of access, no matter if it is stored on prem, on the internet, or in the Cloud.
Contact Us today to find out how Thomas Duryea Logicalis can support you with your organisation's security concerns and posture.



